Why Huawei Cloud QingTian Enclave?
Why Huawei Cloud QingTian Enclave?
Typical Scenarios of Huawei Cloud QingTian Enclave
Typical Scenarios of Huawei Cloud QingTian Enclave

Protection of Private Keys
You can store plaintext private keys of encryption services such as SSL/TLS in QingTian Enclave. QingTian Enclave will ensure no other users or applications can access or view your keys.

Protection of Sensitive Applications and Models
You can run highly sensitive applications or AI models in QingTian Enclave. Other applications, instances, or operations personnel will be completely blocked from access to sensitive data or models.

Secure Multi-Party Computation
With cryptographic attestation of QingTian Enclave, you can set up multi-party computation, where multiple parties can join and process highly sensitive data without having to disclose or share the actual data with each individual party. Multi-party computation can also be done within the same organization to establish separation of duties.
QingTian Enclave Advantages
Securely Isolated Trusted Environment
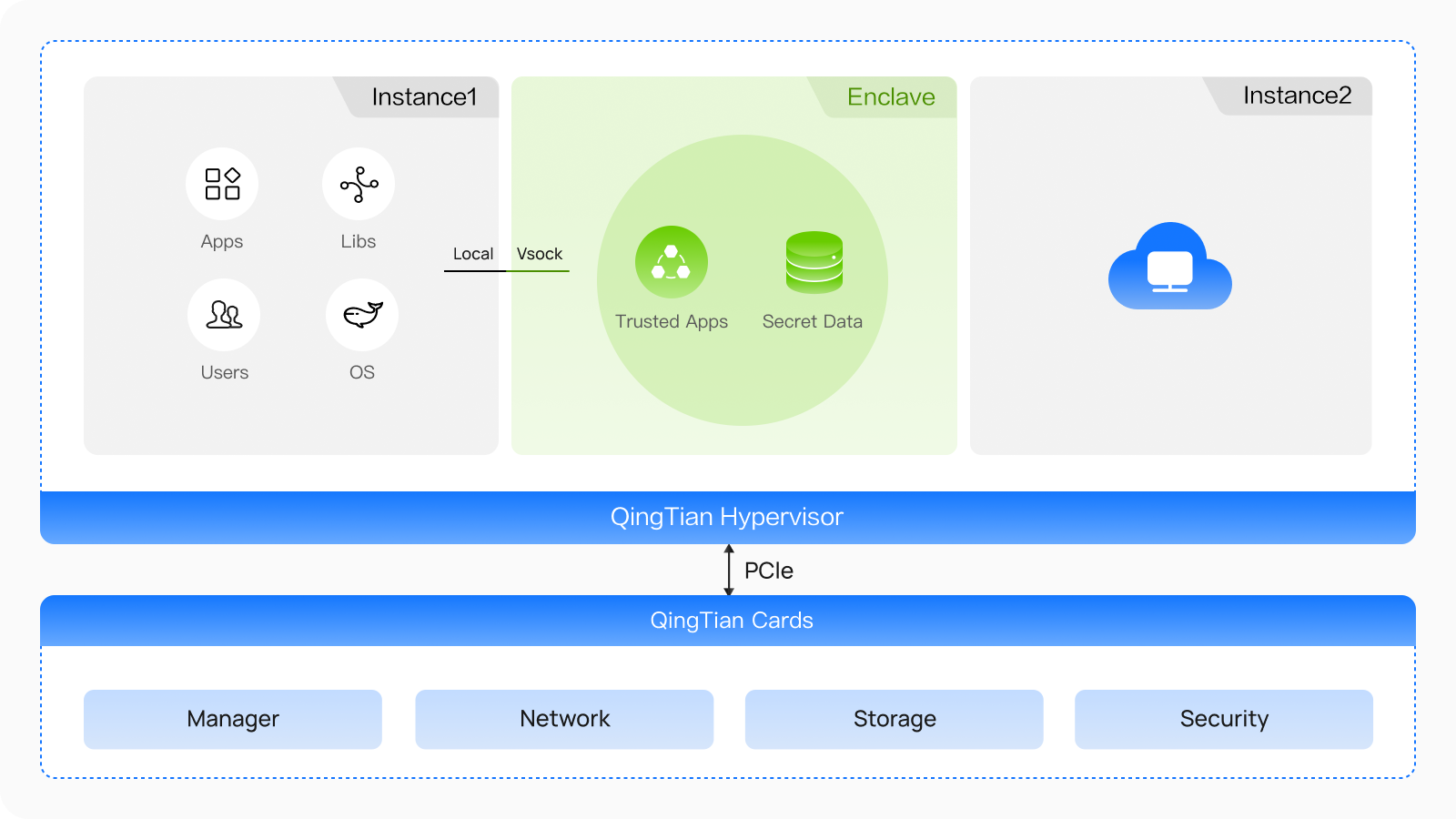
QingTian Enclave is a completely isolated, highly trusted computing execution environment. It has no persistent storage, interactive access, or external network connections. After an isolated enclave environment is created from the parent instance, instructions and applications are delivered to the isolated environment through an encrypted local channel. This greatly reduces the attack surface.

Cryptographic Attestation
QingTian Enclave uses attestation to verify the identity of an enclave and whether only authorized code is running in the enclave. The attestation process is completed through attestation documents, which are generated by the QingTian management program. Attestation documents contain key details of the enclave, such as the enclave's public key and hashes of the enclave image and applications. Huawei Cloud KMS has integrated QingTian Enclave attestation. You can use condition keys in IAM policies to control permissions of a specific enclave on KMS.

Flexibility
You can create QingTian Enclave instances with different combinations of vCPUs and memory. QingTian Enclave combines hardware and software. It is processor agnostic and compatible with any programming language or framework. In addition, since many components of QingTian Enclave are open source, you can even check and verify the code by yourself. You can create multiple separate, isolated QingTian enclaves on a parent instance for confidential computing.

More About QingTian Enclave
More About QingTian Enclave
Getting Started with QingTian Enclave
You can refer to the tutorial to create QingTian Enclave instances and learn how to use QingTian Enclave features.
QingTian Enclave Application Development
QingTian Enclave provides SDKs for you to develop your own QingTian Enclave applications. It also provides a network proxy tool (qproxy), a log forwarding tool (qlog), and a CLI.
QingTian Enclave Cryptographic Attestation
QingTian Enclave supports complete cryptographic attestation. Enclave applications can use attestation documents to verify the identity of enclaves and establish trust with external services.